Security from Ground to Cloud
Ruckus Cloud Infrastructure
Ruckus Cloud provides robust security mechanisms available to protect user traffic and secure the infrastructure.
-
Automatic security updates and patches to the cloud and mobile app
-
State-of-the-art data centers and data processing systems that are protected by firewalls
-
Data is transported over secure protocols and encrypted at rest
-
Secure account credentials, account security protections, change management and control policies
-
Access to customer data restricted to personnel strictly based on business need and limited by functional role
Management and Administration
The customer can delegate the administrative role to a trusted Ruckus VAR, so that the VAR can help manage the customer network. This privilege can be revoked at any time.
Multiple employees can help manage the network. Role-based access control (RBAC) is available for both the customer and the VAR. Administrators can have primary admin, read-write, read-only, or guest roles. The least number of administrative privileges can be implemented for operational security by assigning different responsibilities to the appropriate people.
AP to Ruckus Cloud Communication
-
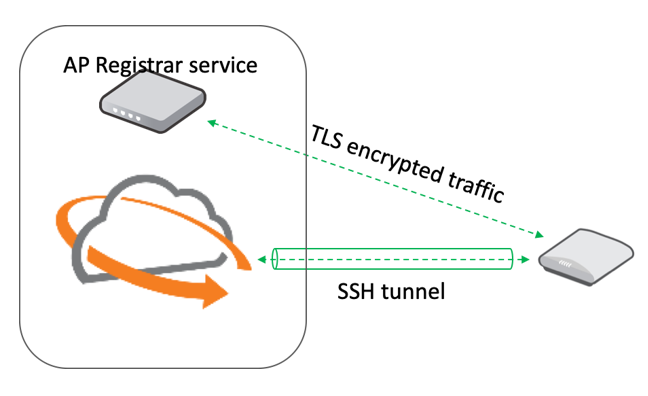
All control traffic is exchanged over an encrypted SSH tunnel.
-
First contact with the AP Registrar occurs over TLS encrypted traffic.
-
Mutual authentication by way of certificates validates the AP to the cloud and vice versa.
-
AP and client management traffic is sent to the cloud.
Secure AP Provisioning
Using the native mobile app, administrators can register an AP by simply "scanning" the barcode using a smartphone camera, eliminating the possibility of manual entry error and automatically activating the Add AP workflow.
Mutual certificate exchanges validate the AP to the cloud and vice versa. Once deployed, all management traffic from the AP to the cloud is encrypted using SSH. Ruckus has a separate AP Registrar service in the cloud. When the serial number is scanned or manually added from the Ruckus Cloud web interface (even before the AP is powered up), the configuration is pushed to the AP Registrar using HTTPS. When the AP powers up, it contacts the AP Registrar service over an HTTPS connection. The AP Registrar validates the AP credentials, and then points the AP to the appropriate controller.
The AP then establishes an SSH connection with the cloud controller and downloads the latest firmware if required. The AP also downloads the latest configuration. All information is exchanged within the secure SSH tunnel if the AP is connected to the cloud.
User Connectivity: Out-of-Band Architecture
User data is sent over the customer network and does not traverse Ruckus Cloud servers except some guest Wi-Fi information required for authentication when captive portal options are used.
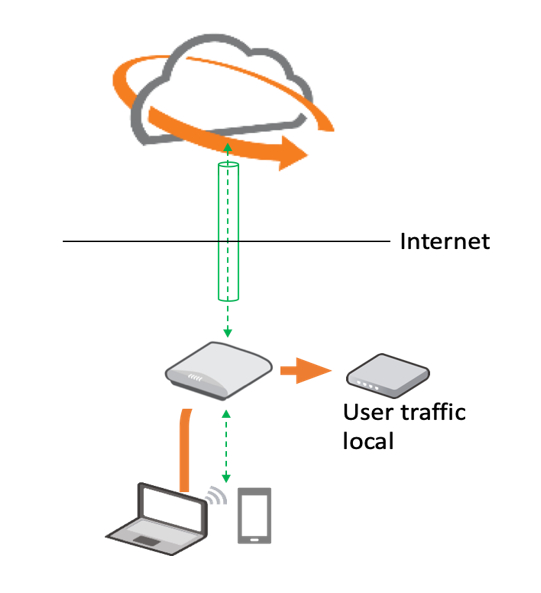
In the cloud architecture, the data plane is local, which means that user data is directly routed to the Internet. In case of guest networks with social media logins, Ruckus Cloud acts as a proxy to exchange credentials between the user and social media platforms (such as Facebook, LinkedIn, Google, and Twitter) over a secure channel. Upon successful authentication, user traffic flows directly to the Internet.
For captive portal networks, authentication requires users contacting the cloud and accepting the terms and conditions. Post-authentication user traffic flows directly to the Internet.
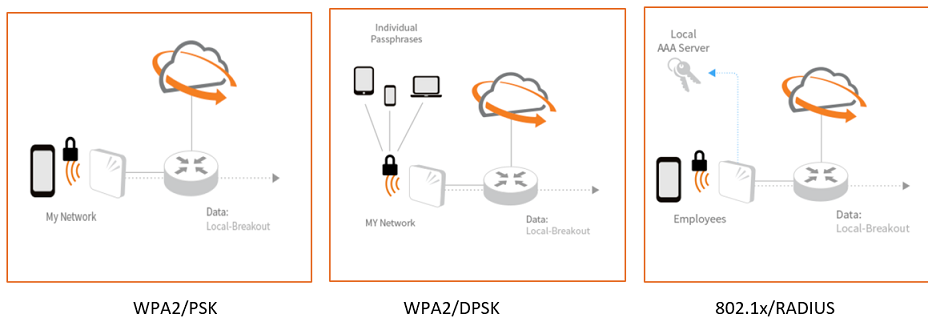
Multiple WLAN Security Types
The Ruckus Cloud has many WLAN types to keep user traffic secure.
-
802.1X networks with local RADIUS: Provides enterprise-grade security with EAP authentication and AES encryption. It can also provide dynamic VLAN options.
-
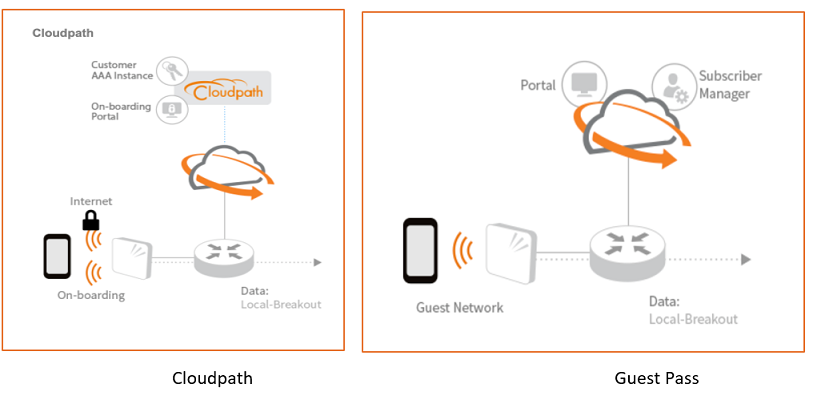
Cloudpath integration with PKI and EAP-TLS: Offers granular policies and a wide breadth of security and encryption options, including certificates at the device level.
-
PSK, 802.1X, and Cloudpath authentication: Fully survivable, they can maintain normal operations even during loss of connectivity to the Ruckus Cloud.
-
Dynamic Pre-Shared Key (DPSK): Each user on the network has an individual passphrase to securely connect to the network. It is equivalent to every user having exclusive secure connectivity with distinct keys from every other user on the same network. Ruckus Cloud automatically generates passphrases of configurable complexity for ease of use. Unlike a traditional PSK network, if a single user key is compromised, the entire network security is not compromised. DPSK requires cloud connectivity for key assignment and is not survivable if there is a loss of connectivity to the Ruckus Cloud.
Additional Security Settings in the Network
Using the advanced network settings, it is possible to set access control policies at the Layer 2 and Layer 3 and Layer 4 levels.
-
With the Layer 3 and Layer 4 access rule, you can allow or block specific protocols between any IP address or IP address range including a port number.
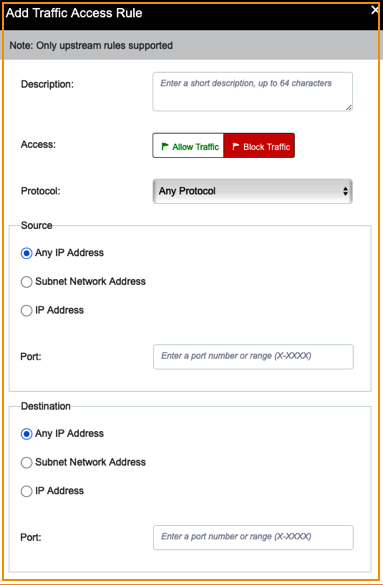
-
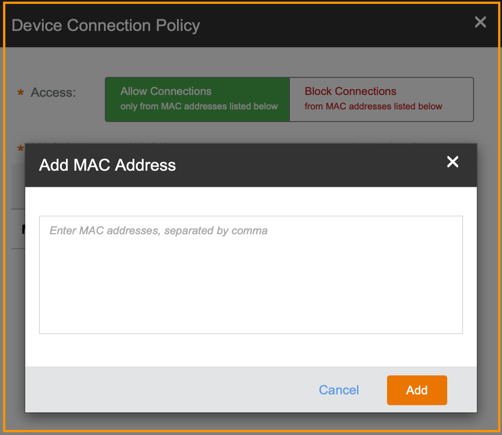
With the Layer 2 connection policy, you can allow or block specific MAC addresses (endpoint devices) from connecting to the network. You can enter multiple MAC addresses at one time with up to 128 addresses in total.
Best Practices for WLAN Security
-
Dynamic VLANs for users from RADIUS: Ruckus recommends isolating client traffic using VLANs. Segregating wireless and wired traffic can give a performance benefit and reduce the possibility of broadcast flood that can render Wi-Fi unusable.
-
WLAN scheduling: An open Wi-Fi available 24x7 can be an exposure risk. A schedule enables or disables WLAN availability automatically.
-
Guest pass management: Guest passes can have timed expiries or passwords regenerated, forcing re-authentication or re-issuance of a pass. Guest users can be disconnected from the network if necessary, preventing any misuse or reuse without administrative knowledge.
-
Hide SSID: Hiding the SSID prevents unknown users from attempting to connect to WLANs.
-
Client isolation: Isolating clients prevents direct communication between devices and is a prudent choice in a guest network when unknown users are joining the same network. Client isolation prevents bridging traffic directly between guests.
Highlights
-
Access points discover and exchange data with the cloud over a secure tunnel.
-
Out-of-band architecture is used where user data is directly routed to the Internet.
-
User data is securely transported and encrypted at rest.
-
Multiple WLAN types provide site-survivable options for administrators to secure wireless data while continuing to serve clients in case of WAN failure or loss of cloud connectivity.
-
The Ruckus Cloud has been designed and built to ensure security from the ground (client devices) to the cloud.
