Managing Guest Users
-
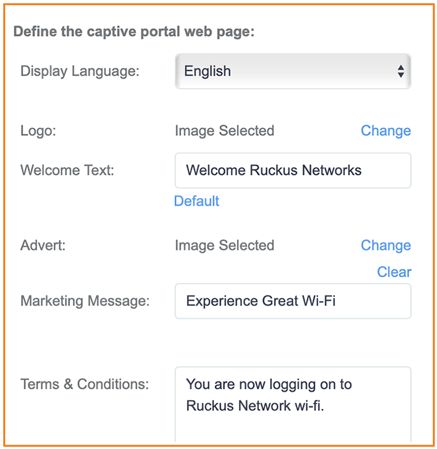
Provide the portal customization settings for all guest WLAN type except the 3rd-Party Captive Portal (WISPr) type.
Figure 118 Captive Portal
-
Under
Advanced Network Settings, configure the user connection options.
Figure 119 User Connection Options
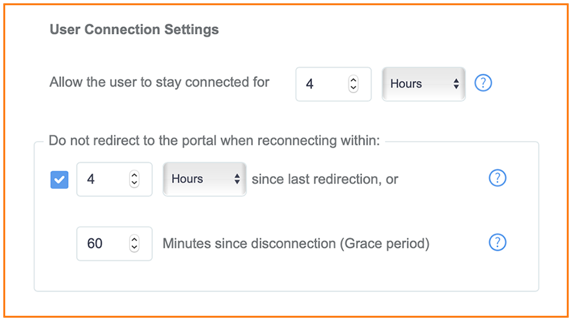
- Indicate the total period of time you want the guest users connected to the network.
-
If configuration for a returning guest user, indicate the period of time until you do not need them to reauthenticate through their captive portal. The client MAC address is cached for this time period, so the user is recognized without reauthentication.
- Set the grace period is set also for a returning user to get back on the network without reauthentication.
Self Sign In login options include social media and SMS tokens. The total number of devices per user can be configured under Advanced Network Settings: for example, the total number of devices allowed on the network with the same social media login or SMS token. token.Figure 120 Guest User Lock Out Setting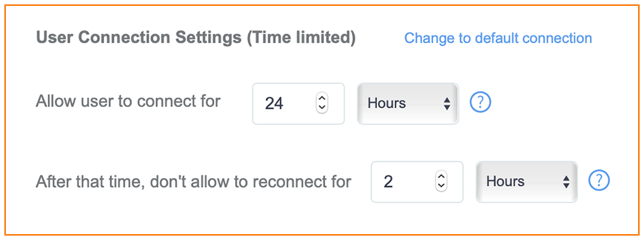 All connected guest users are listed under Users > Clients.Figure 121 Maximum Number of Devices
All connected guest users are listed under Users > Clients.Figure 121 Maximum Number of Devices Guest users connected using Self Sign In and Guest Pass are listed in the Guest Passes tab.Figure 122 Connected Clients
Guest users connected using Self Sign In and Guest Pass are listed in the Guest Passes tab.Figure 122 Connected Clients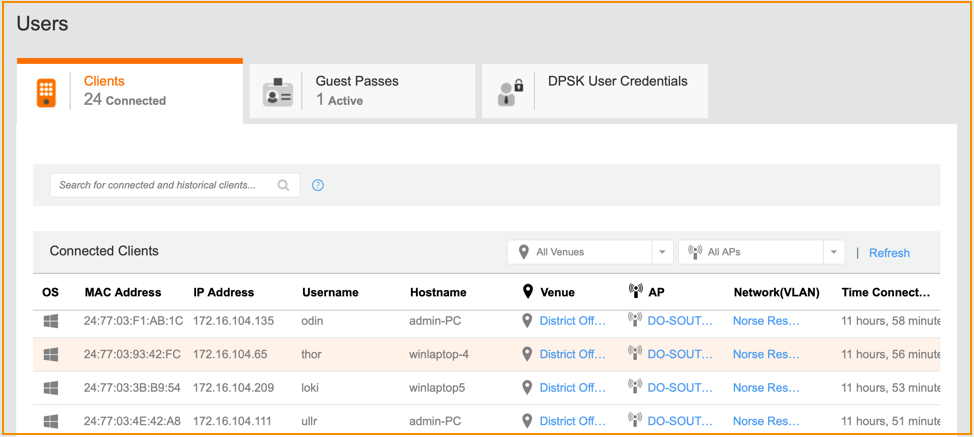 Every guest pass that is created can be shared through SMS messaging, a hassle-free option for organizations that do not have to deal with Twilio worldwide.Figure 123 Guest Passes
Every guest pass that is created can be shared through SMS messaging, a hassle-free option for organizations that do not have to deal with Twilio worldwide.Figure 123 Guest Passes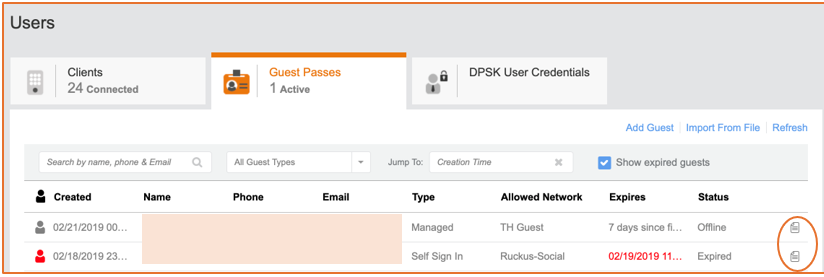
-
Click the
Note icon in the upper-right corner of the page to manage guests.
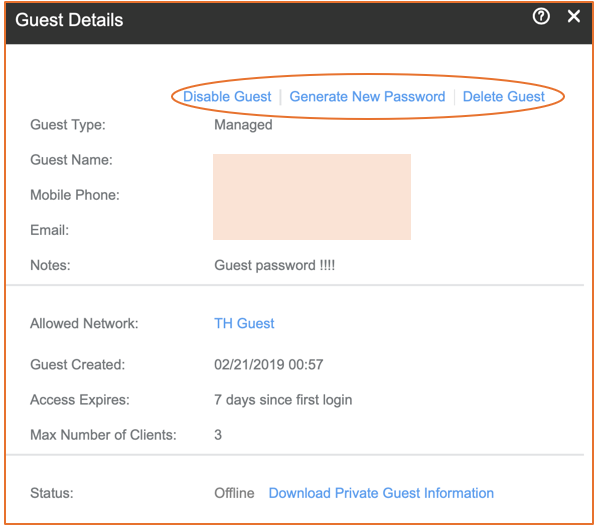
- The Guest Pass is a managed type of WLAN because the administrator creates and shares the guest passes. The administrator can disable or delete the guest user, and regenerate a password to share with user based on prior settings.
Figure 124 Guest Details
- The
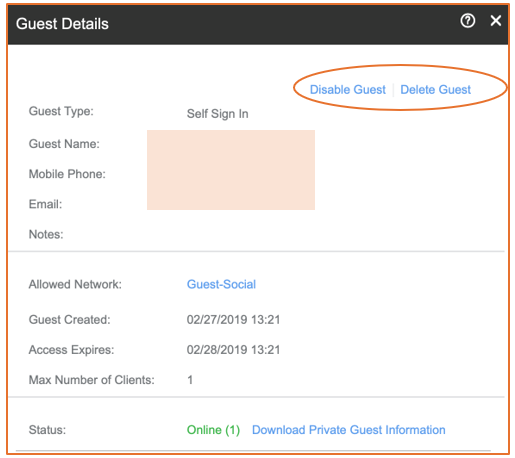
Self Sign In type of WLAN allows guest users to log in through their personal accounts. Therefore, the administrator can only disable or delete the guest user.
Figure 125 Disabling or Deleting a Guest User
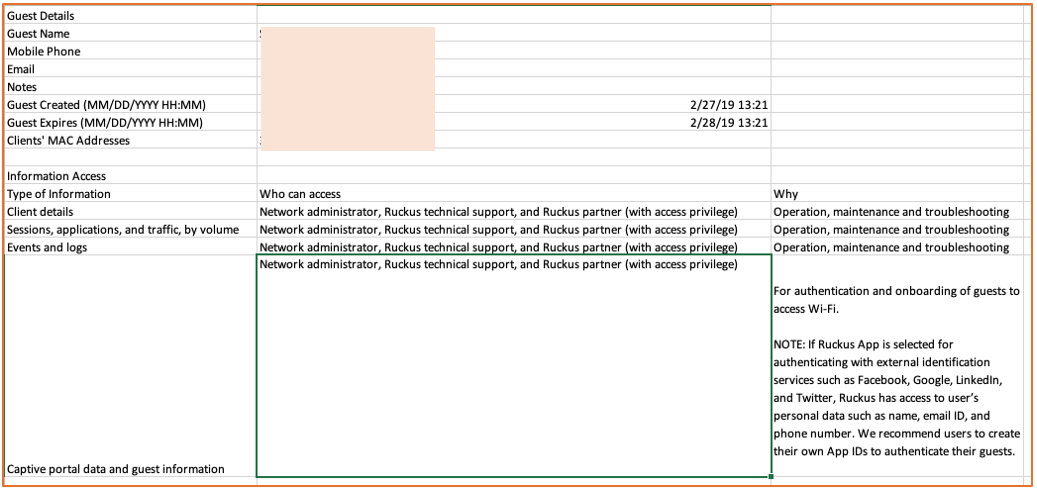
- The information for each guest user can be downloaded (in compliance with GDPR requirements).
Figure 126 Guest User Information
All these configuration options are designed to simplify guest management for IT administrators, and provide them sufficient control over the users and connections on the network.
- The Guest Pass is a managed type of WLAN because the administrator creates and shares the guest passes. The administrator can disable or delete the guest user, and regenerate a password to share with user based on prior settings.
Parent topic: WLAN-Specific Guest Management
