Access Policies
- From the navigation pane, click
Services. The Services page appears.
- Select the Access Policies sub-tab. The Access Policies page appears.
Access Policies 
- Select the Device connection sub-tab to add a
device connection policy.
- Click Add
Policy corresponding to Device Connection
Policy. The Device Connection Policy dialog box is displayed.By default, the Allow Connections only from MAC addresses listed below option (green) is enabled. You can choose to change this to Block Connections from MAC addresses listed below by clicking the option (red) provided.
- Enter a name in the Policy Name field.
- Add a brief description in the Description field.
- Click Add to add a MAC addresses.
- Enter the MAC addresses in Add MAC Address dialog box and click Add.
- Click Clear list to clear the MAC address list.
- Click OK to
return to the Edit Network screen. Note: As an admin user, you can assign a single policy of each type to the network as the default policy or as part of the Network and Venue activation. This action overrides the default network policy.
- Click Add
Policy corresponding to Device Connection
Policy.
- Select the Traffic Policy sub-tab to add a traffic
policy.
- Click Add Policy. The Traffic Control Policy dialog box is displayed.
- Enter a name in the Policy Name field.
- Add a brief description in the Description
field.By default, the Allow Traffic option (green) is enabled. You can choose to change this to Block Traffic by clicking the option (red) provided.
- To create a new traffic rule, click the Add Rule
link. The Add
Traffic Access Rule dialog box is displayed. You can
create rules only for up-stream traffic. Complete the following steps.
- Description: Enter a description for the rule.
- You can create a rule to allow or block up-stream traffic by clicking and selecting the Allow Traffic or Block Traffic option, respectively.
- Select the protocol
which you wish to use for the new traffic rule, from the
Protocol drop down list. Following are the list
of protocols available for use.
- TCP: Transmission Control Protocol
- UDP: User Datagram Protocol
- UDPLITE: Lightweight User Datagram Protocol, which is a connectionless protocol that allows even a damaged data payload to be delivered rather than being discarded.
- ICMP (ICMPV4): Internet Control Message Protocol, which is an error-reporting protocol used by network devices to generate error messages to the source IP address, when issues in the network prevent delivery of IP packets.
- IGMP: Internet Group Management Protocol, which is a communications protocol used by hosts on IPv4 networks to establish multicast group memberships.
- ESP: Encapsulating Security Payload is a protocol which provides the authentication, integrity, and confidentially of network packets in IPv4 and IPv6 networks.
- AH: Authentication Header protocol, which is used to authenticate SNMP.
- SCTP: Stream Control Transmission Protocol is a communications protocol which operates at the transport layer.
- Specify the source address in the Source field. You can either specify a range (a network address and a Subnet Mask, in the field provided) or you an specify a source IP address in the field provided. Also, specify a port number or a range of ports (for example, 22-34) for the source, in the field provided.
- Specify the destination
address in the Destination field. You can either specify a
range (a network address and a Subnet Mask, in the field
provided) or you an specify a source IP address in the field
provided. Also, specify a port number or a range of ports (e.g:
22-34) for the destination, in the field provided. Note: If you choose the ICMP protocol in the previous step, you do not need to specify ports for the source and the destination. Hence, the option to select ports will not be presented to you.
- Click Save. The rule which you created appears
in the Traffic Control Policy dialog box. Note: The rule which you initially create appears in a row with priority set a "1", by default. When you create a second rule, it appears in the row with priority "1" and the previous rule which you created appears as second in the row, with priority "2". When you have multiple rules created, you can use the "up" and "down" arrows available at the end of each row, to shift respective rows up or down in the order, to set the desired priority.
The edit and delete links available at the end of each row allow you to edit and delete respective rules. Each time you click the edit button, the Add Traffic Access Rule dialog box is displayed. where you can edit any of the rule properties.
- Click OK in the Traffic
Policy dialog box, once you have all the required rules
added. You are navigated back to the Advanced Network Settings dialog box, where are can click the Traffic Policy toggle button to ONor OFF, activating or de-activating the traffic policy which you created, respectively. The Edit option allows you to navigate to the Traffic Control Policy dialog box, where you can edit the policy which you created. The Clear button allows you to delete the traffic policy.
- Select the Device & OS Access Policies sub-tab to add a
device and OS access policy. The Device & OS Access Policies dialog box appears.
Device & OS Access Policies 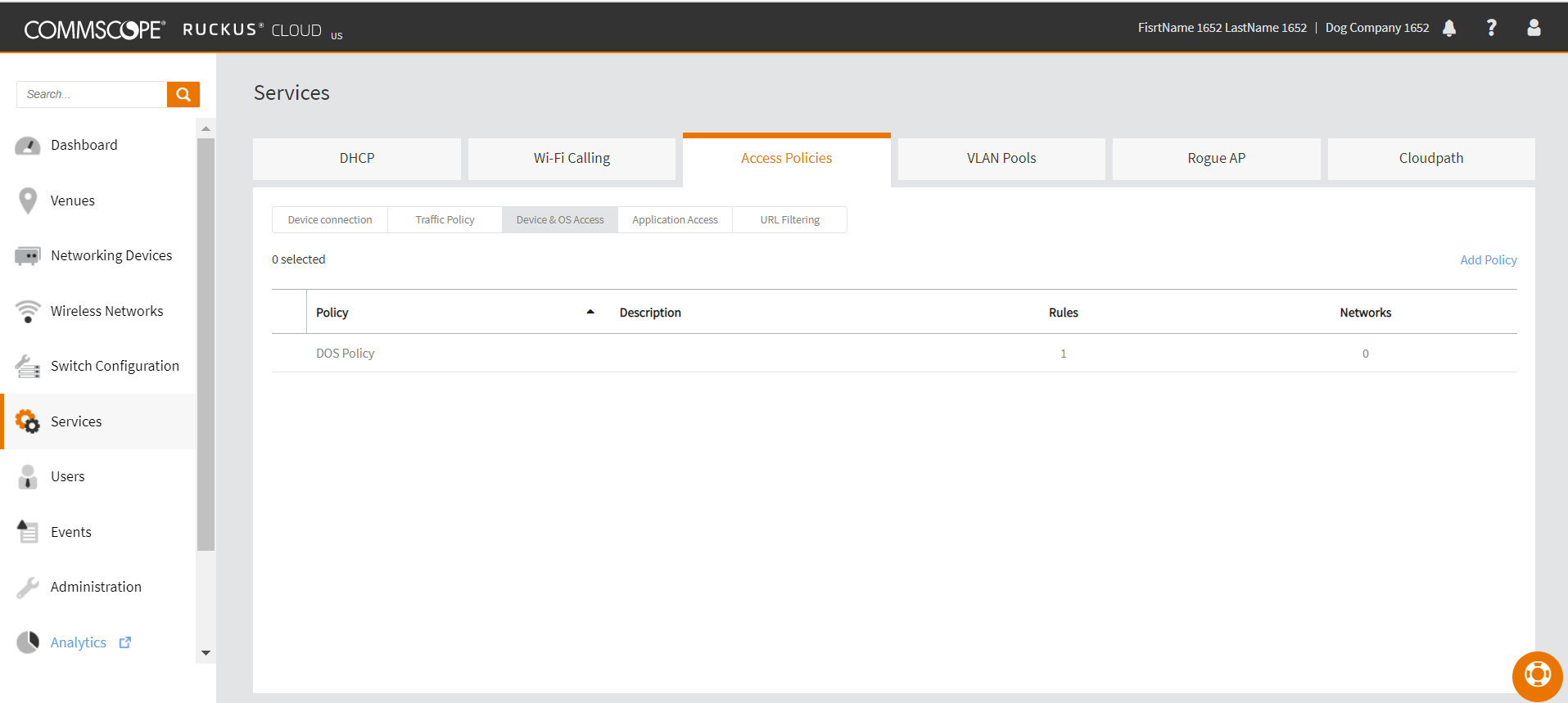
- To add a Device & OS Access Policies, click Add
Policy. Add Device & OS Access Policies dialog box appears. Complete the following:
- Policy Name: Enter the name of the policy.
- Description: Enter description for the policy.
- Default Access: Select either Allow or Block.
Adding Device & OS Access Policies 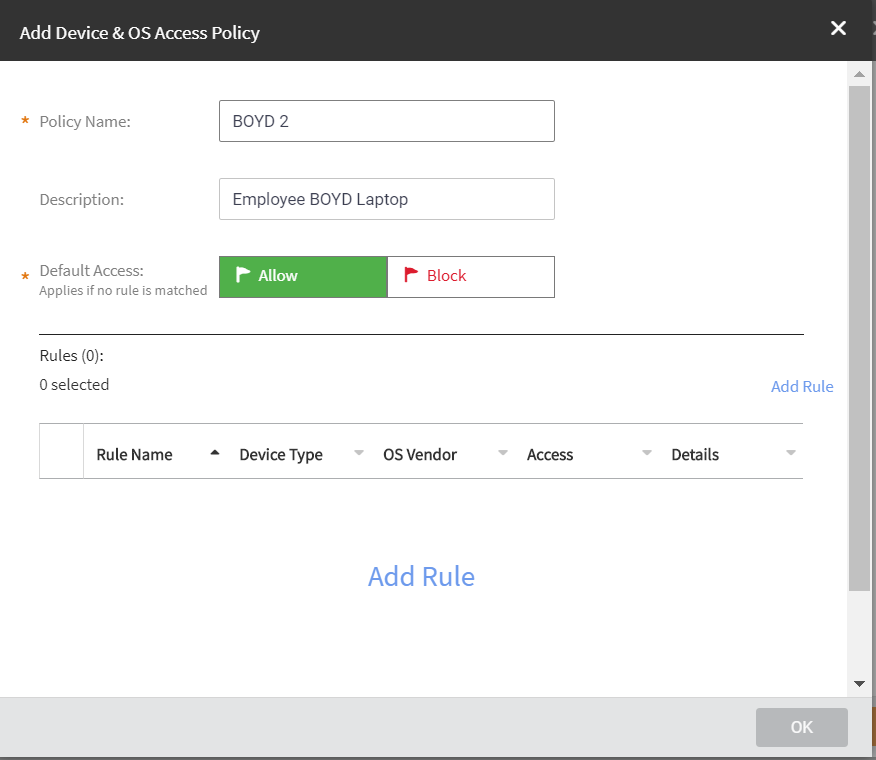
- To add a Device & OS Access Policies, click Add Policy.
- Click Add Rule.The Add Rule dialog box appears. Complete the following:
- Rule Name: Enter the name of the rule.
- Action: Select either Allow Devices or Block Devices.
- Device Type: Select a device type from the list of devices.
- OS Vendor: Select the OS vendor for the devices.
- Rate Limit: Configure the late limit using the sliders: From client and To client.
- VLAN: Enter the VLAN ID.
Adding Rule for Device and OS access Policies 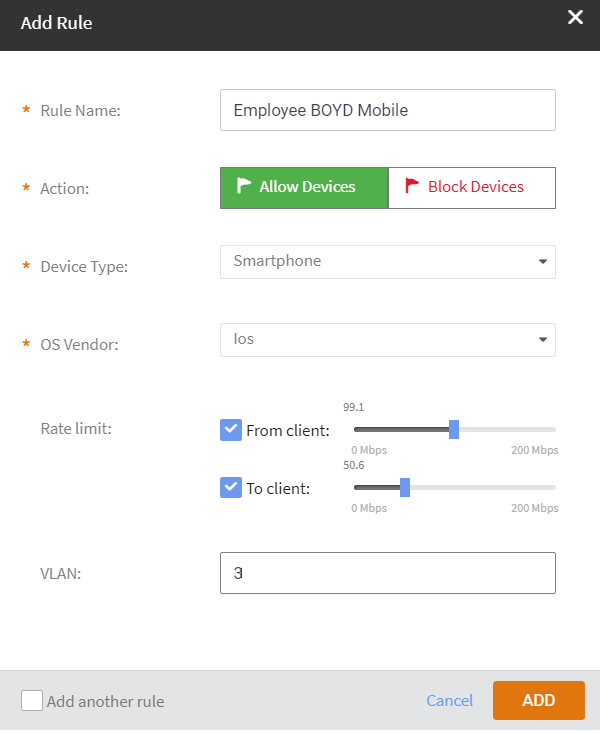
- Click ADD. Returns to Add Device & OS Access Policies dialog box.
- Click OK to add the rule to return to the Device & OS Access Policies page.
- To add a Device & OS Access Policies, click Add
Policy.
- Select the Application Access sub-tab to add an aplication
policy.The Application Access policies page appears.
Applicatinon Access 
- Click Add Policy to add an application access policy.
- Enter a name in the Policy Name field.
- Add a brief description in the Description field.
- Click Add Rule and configure the following in the
Add Application Rule dialog box.
- Rule Name: Enter the name of the rule.
- Rule Type: Select System Defined or User Defined.
- Application Category: Select the category of application from the drop-down.
- Application Name: Specify the name of the application.
- Access Control: Configure the method as Block Application, Rate Limit or QoS.
- Click ADD.