Configuring SAML SSO with Azure AD
Azure Active Directory (AD) is a cloud-based application that helps in identity and access management by storing information about members of the domain (such as users and devices), verifying their login credentials, and controlling their access privileges. This section provides details on how to configure Azure AD as an identity provider (IdP) and integrate SAML single sign-on (SSO).
Azure AD is now known as Microsoft Entra ID and in this document you may see one or both names depending on the task being performed.
-
On the Azure Portal home page, click or search for Microsoft Entra
ID. The Overview page for your Active
Directory is displayed.
Microsoft Azure Home Page 
-
In the navigation pane, select
Enterprise
applications and then click + New application
on the All applications page. The Browse
Microsoft Entra Gallery page is displayed.
Enterprise Applications |All applications - New Application 
-
Click Create your own
application. The Create your own application
window is displayed.
Create Your Own Application Window 
-
Complete the following fields:
- Name: Enter a name for the application.
- Select Integrate any other application you don't find in the gallery (Non-gallery) option. Leave the other options as is.
- Click Create to create the application. The application is registered in Azure AD for authentication.
-
In the navigation pane, select
Enterprise
applications and click the new application. The application
overview page is displayed.
Application Overview 
-
Click Users and groups
in the navigation pane or click Assign users and
group in the Getting Started
section to add users and groups of users to the application.
Add User/Group 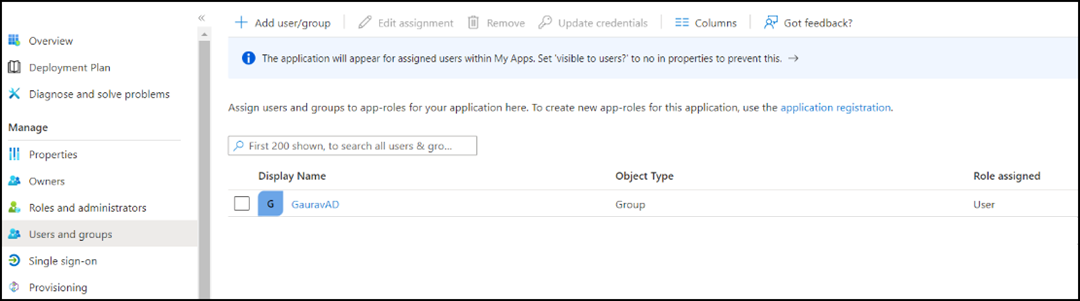
-
In the Users and
groups page, click Add user/group.
The Add Assignment page is displayed.
Assigning Individual Users and User Groups to the Application 
- Click None Selected to display the Users and groups sidebar. Click the checkbox next to the desired group names to list them on the Selected pane and click Select to add the selected groups to the application. The selected groups are displayed in the Add Assignment page and the Assign button is enabled.
- Click Assign to assign the groups to the application.
-
Select a group and click
Add members. The Add members
page is displayed. Select the checkbox against a user to list them on the
Selected pane and click Select to add the selected member to
the group.
Note: You can click on specific group to view the properties of the group. Take note of the Object Id of the group as you will require to enter it into the Group ID field in RUCKUS One while creating an SSO Group. For more information, refer to Adding and Managing an SSO Group.
Group Properties 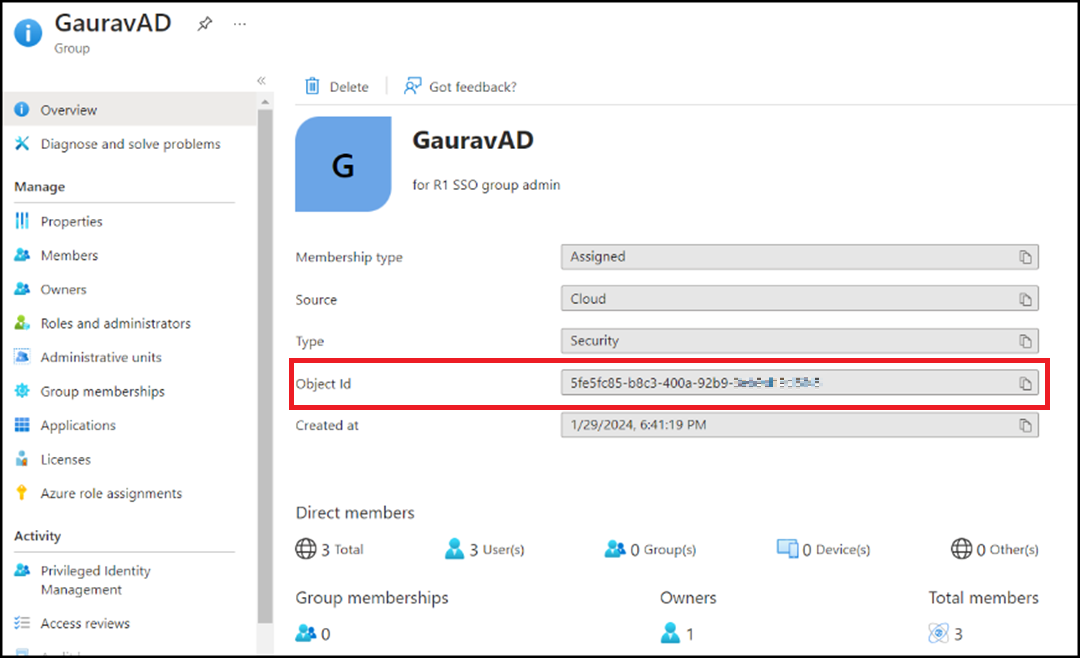
-
In the navigation pane, select
Enterprise
applications and click the application. The application overview
page is displayed.
Application Overview 
-
Select Single sign-on in
the navigation pane and click SAML protocol in
the Select a single sign-on method window. The
SAML-based Sign-on page is displayed.
Selecting SAML as Single Sign-On Method 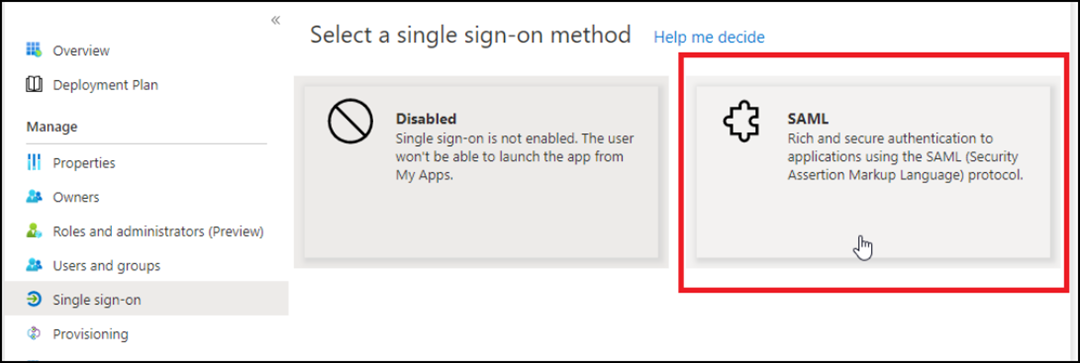
-
Click Edit in the top
right corner of the first section, Basic SAML
Configuration.
In the Reply URL (Assertion Consumer Service URL) field, specify a valid redirect URL where the authorization server sends the user once the application is successfully authorized. For example, https://ruckus.cloud/login/saml2/sso/<tenant-id>.
The tenant ID is a unique identifier for the tenant account. Refer to User Profile to view your tenant ID.
Alternatively, you can view the tenant ID in the Address bar of the browser screen. Once you log in to the RUCKUS One Cloud portal, you can find the Tenant ID in the URL. For more information, refer to: https://support.ruckuswireless.com/articles/000006453.Locating the Tenant ID 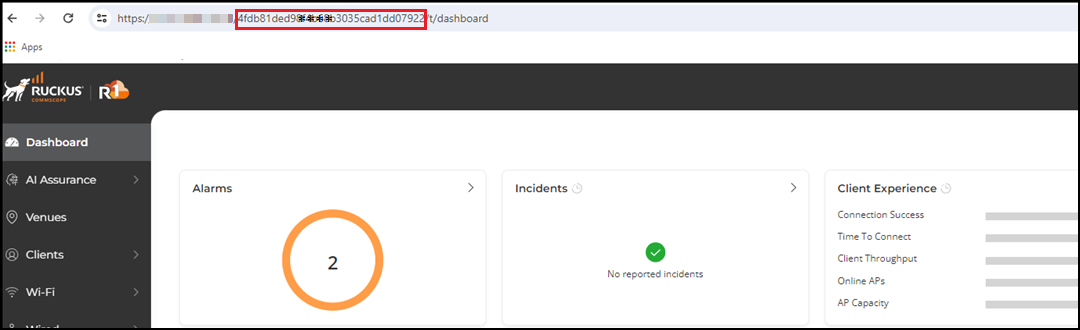
Editing Basic SAML Configuration 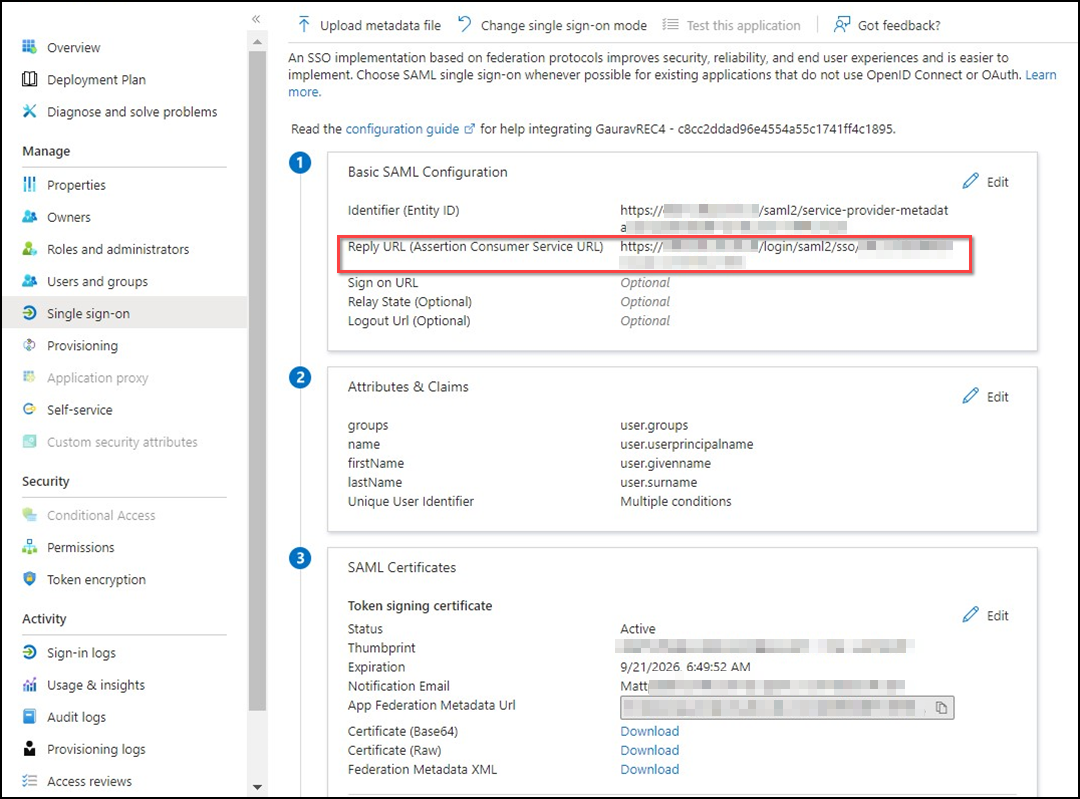
-
Click Edit in the
second section, Attributes and Claims, and make sure to add
a group claim as the SAML assertion requires an attribute to relay the group
information.
Note: RUCKUS recommends that you complete and review your account information. The following settings must be configured exactly as specified:
- email (user.mail): The primary email address for login. This is a mandatory field.
- name
(user.userprincipalname): This serves as the unique
identifier for the user in Azure AD. It is formatted as
username@yourdomain.com. This is also a mandatory field. - firstName (user.givenname): The first name of the user.
- lastName (user.surname): The last name of the user.
- groups (user.groups): Dynamic groups allow you to define rules based on various user attributes like user.mail, user.givenname, user.surname, and so on. Users who meet these criteria automatically become members of the group.
Attributes and Claims - Adding Group Claims 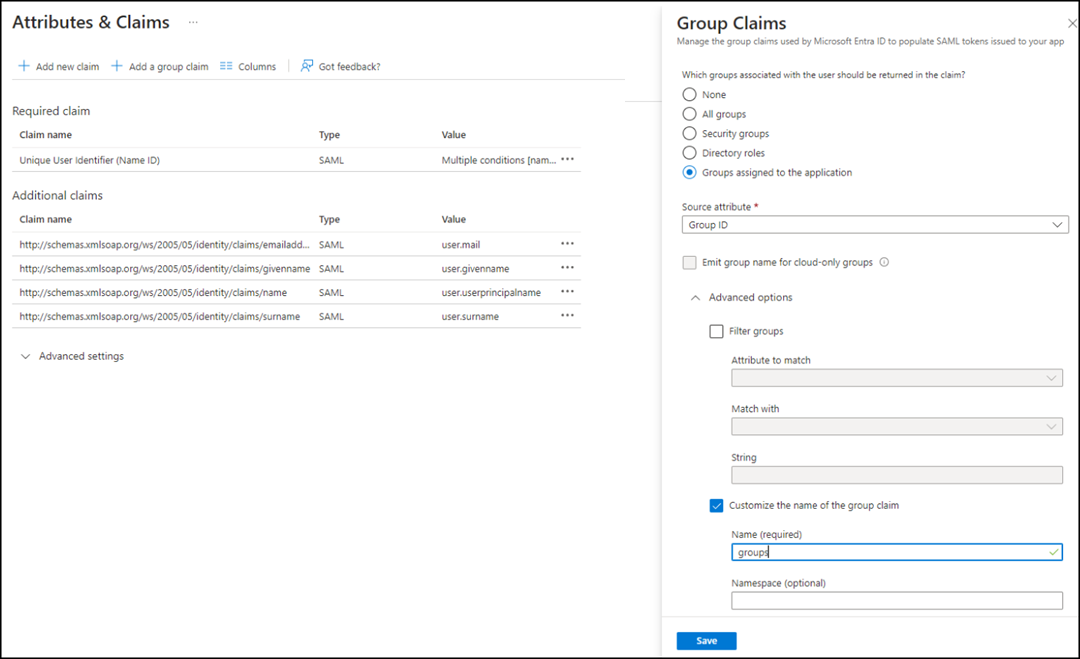
- In the Attributes and Claims page, click Add a group claim. The Group Claims sidebar is displayed.
- Select Groups assigned to the application to specify which groups you would like to return in the Group Claims settings.
- Select Group ID as the Source attribute.
- Select Customize the name of the group claim and enter a name for the group in the Name field.
- Click Save to add the group claim.
-
In the third section,
SAML Certificates, under Token signing
certificate, either copy the App Federation Metadata URL or
download the Federation Metadata XML file. The IdP Metadata needs to be uploaded
to RUCKUS One while setting up Setting Up SSO. For more information, refer to
Setting Up SSO with a 3rd Party Provider.
Copy or Download IdP Metadata 
-
(Optional) If the SAML sign-on
requests to Azure IdP must be signed for added security, complete the following
steps:
-
Click the Edit icon
in the Verification certificates section. In the
Verification certificates sidebar, select the
Require
verification certificates checkbox.
Verifying a SAML Certificate 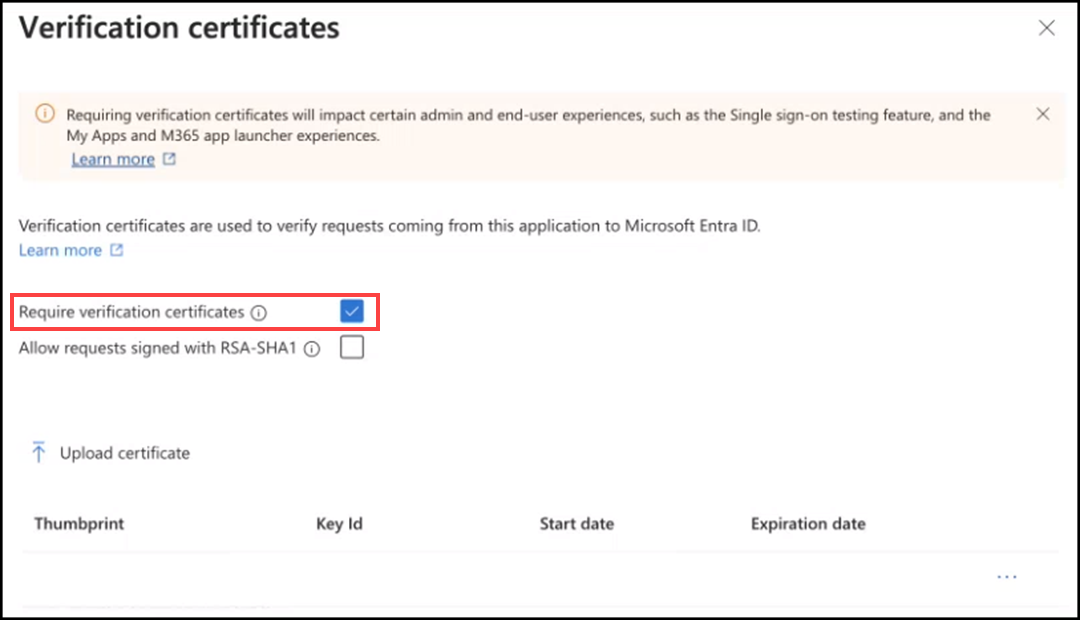
- Open the RUCKUS service provider (SP) metadata XML document.
- Copy the certificate string and use an online tool, such as https://www.samltool.com/format_x509cert.php, to convert the string to an RSA file format.
-
Save the certificate
string found in the
X509Certificatefield as a .CER file. - In the Verification certificates sidebar, click Upload certificate to select the .CER file and add to the list of verification certificates.
-
Click the Edit icon
in the Verification certificates section. In the
Verification certificates sidebar, select the
Require
verification certificates checkbox.
-
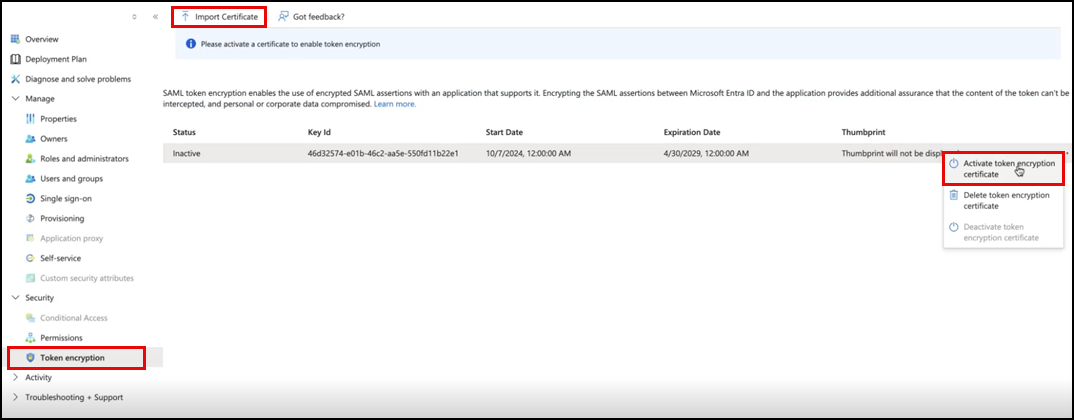
(Optional) If you want to
decrypt an encrypted SAML response, complete the following steps:
- Generate a public server certificate using the public API (https://docs.ruckus.cloud/api/) and download the server certificate.
- To import the public server certificate (.CER), go to the Azure AD application page, from the navigation bar, select Security > Token Encryption section. In the Token Encryption page, click Import Certificate. In the Import Certificate dialog box, browse to the server certificate and click Import. The public server certificate is imported.
- To activate the token encryption, click the three dots next to Thumbprint and select Activate token encryption certificate. A success message is displayed upon successful token encryption activation.
Token Encryption