Creating a Network That Uses an Enterprise AAA Server
You can create a network that authenticates users against a remote Authentication, Authorization, and Accounting (AAA) server. Before you begin, note the IP address, port, and shared secret for your primary and (if applicable) secondary RADIUS servers.
In non-proxy mode, an AP sends the RADIUS requests directly to the RADIUS server. The outbound connection is from the AP to the IP/FQDN of the RADIUS server on the RADIUS port used by the RADIUS service. If this is an Internet or external RADIUS system, the APs must be able to reach the server from their locations, for example, via NAT or public routing.
For proxy mode, the controller sends the outbound RADIUS queries on behalf of the AP to the RADIUS server. Therefore, in this mode, the cloud controller performs the outbound connection on the required port, and customers do not need to configure firewall rules, since the cloud initiates the request. If you are hosting the RADIUS system, you must allow inbound connectivity to a routable or NATed IP address on the RADIUS port configured in the WLAN. In proxy mode, all the RADIUS requests from the AP to the controller pass over the existing control tunnel.
-
In the navigation bar, select
Wi-Fi > Wi-Fi
Networks > Wi-Fi Networks
List.
The Wi-Fi Networks page is displayed.
-
Click Add Wi-Fi
Network. Alternatively, select an Enterprise AAA (802.1X) network
from the network list by clicking the radio button next to the Name column and
then click Clone.
The Create New Network page is displayed.
-
Complete the following settings
on the Network Details page.
- Network Name: Enter a name (2 to 32 characters) for a network. By default, this name is also used as the SSID.
- Set different
SSID: (Optional) Click Set different
SSID to configure an SSID different from the network
name. The SSID field is displayed.
- SSID: Enter an SSID name (2 to 32 characters).
- Description: Enter a description (up to 64 characters) to help you identify the network.
- Network Type: Select Enterprise AAA
(802.1X). A structure diagram of an Enterprise AAA (802.1X) is displayed.Note: If you used the Clone option, the Network Type is already set to Enterprise AAA (802.1X).
Create New Network - Network Details 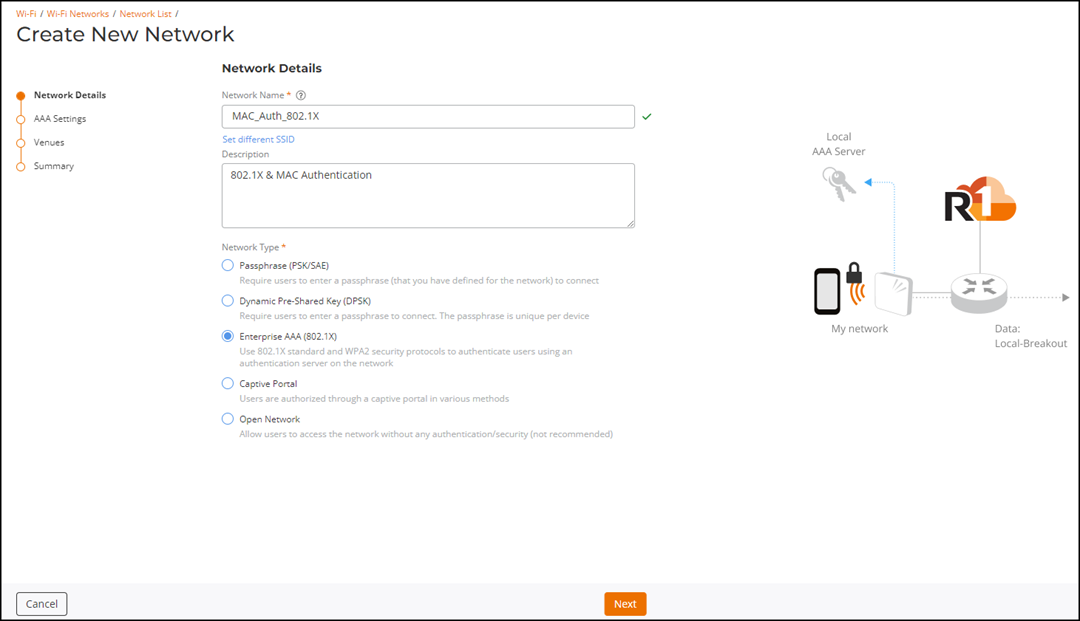
-
Click Next.
The AAA Settings page is displayed.
Create New Network - AAA Settings 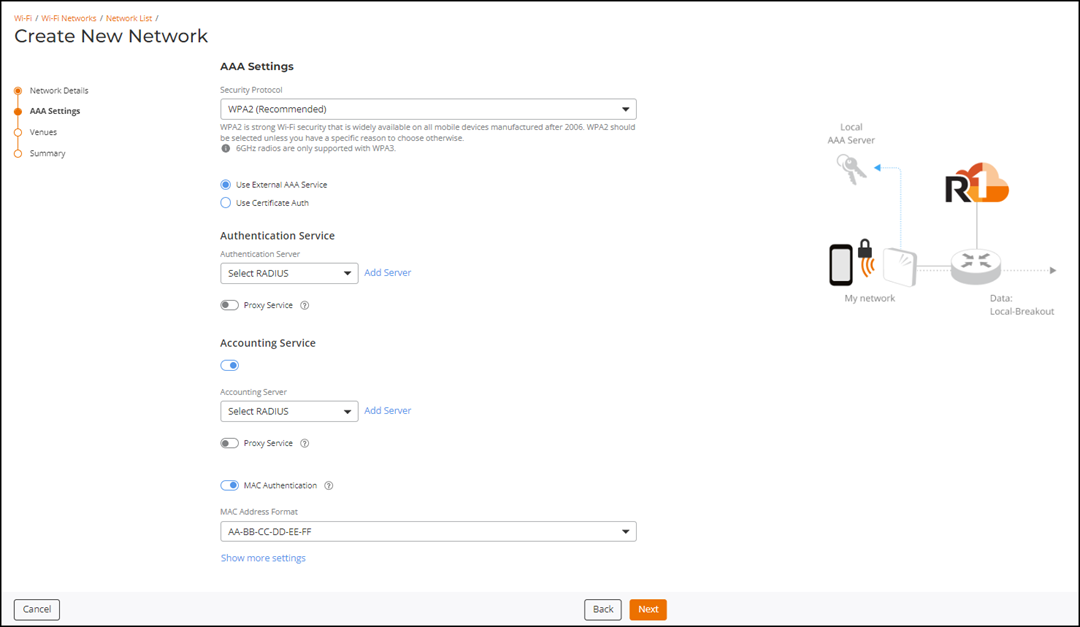
-
Security Protocol: Select the security protocol from the
drop-down list. The options are:
- WPA2 (Recommended) (Default)
- WPA3
- WPA2/WPA3 mixed mode
Note: WPA2 provides strong Wi-Fi security and is supported on all mobile devices manufactured after 2006, making it the recommended choice unless there is a specific need for an alternative. Devices with 6 GHz radios require WPA3, which offers the highest level of Wi-Fi security but is only supported on devices manufactured after 2019. WPA2/WPA3 mixed mode allows devices to connect using either WPA3, the most secure standard, or WPA2, which remains widely compatible. -
Encryption Type:
This field appears only when WPA3 is selected. Choose an encryption type from the drop-down
list:
- AES (default)
- AES-GCMP-256
Create New Network – Encryption Type for WPA3 in the AAA Settings Page 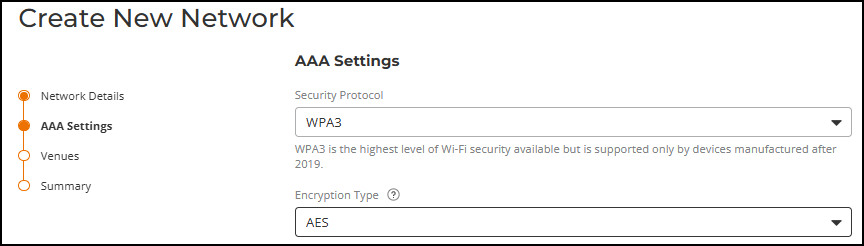 Note: 11ac Wave 1 APs do not support the AES-GCMP-256 encryption type, and therefore cannot operate on SSIDs that use this encryption. For a list of Wi-Fi 11ac Wave 1 indoor and outdoor APs supported by RUCKUS One, refer to https://www.ruckusnetworks.com/ruckus-one-supported-network-devices.Note: When AES-GCMP-256 encryption is selected, the 802.11r Fast BSS Transition option does not appear in the Networking section under Show more settings.Note: According to the WPA3 Specification (version 2 or later), AES-GCMP-256 only supports the following cipher suites. Depending on the client type and OS, some clients may refuse to connect to the WLAN if your RADIUS server does not use one of these required cipher suites:
Note: 11ac Wave 1 APs do not support the AES-GCMP-256 encryption type, and therefore cannot operate on SSIDs that use this encryption. For a list of Wi-Fi 11ac Wave 1 indoor and outdoor APs supported by RUCKUS One, refer to https://www.ruckusnetworks.com/ruckus-one-supported-network-devices.Note: When AES-GCMP-256 encryption is selected, the 802.11r Fast BSS Transition option does not appear in the Networking section under Show more settings.Note: According to the WPA3 Specification (version 2 or later), AES-GCMP-256 only supports the following cipher suites. Depending on the client type and OS, some clients may refuse to connect to the WLAN if your RADIUS server does not use one of these required cipher suites:- TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384: ECDHE and ECDSA using the 384-bit prime modulus curve P-384.
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384: ECDHE using the 384-bit prime modulus curve P-384 and RSA ≥ 3072-bit modulus.
- TLS_DHE_RSA_WITH_AES_256_GCM_SHA384: RSA ≥ 3072-bit modulus and DHE ≥ 3072-bit modulus.
-
Use External AAA
Service: By default, Use External AAA
Service is selected.
If you want to use a certificate authority, select Use Certificate Auth and select up to five certificate templates from the Certificate Template drop-down list or click Add to add a certificate template. Refer to Adding a Certificate Template for instructions on how to add a certificate template.
-
Identity
Group: Select an identity group from the drop-down or click
Add to
add an identity group. Refer to Adding an Identity Group for
instructions on how to add an identity group. To view details about the identity
group, click View
Details.
The Identity Group sidebar is displayed.Note:
- When an identity group is selected, all devices joining the network automatically become an identity within that group, as displayed on the Identity Group page.
- Users have the option to either select an existing identity group from the list or create a new one.
- During network editing, the originally selected identity group cannot be removed, but it can be changed to a different identity group.
- The identity configuration section is not applicable to the MAC Registration List when MAC Authentication is enabled.
-
Authentication
Service: Select an existing RADIUS server from the drop-down
list or complete the following steps to add a new RADIUS Server.
-
Click Add
Server and configure a new RADIUS Server. Refer to Adding and Managing a RADIUS Server.
-
Proxy
Service: Toggle the switch on to enable the proxy
service.
Note: Use the controller as a proxy in 802.1X networks. A proxy AAA server is used when APs send authentication/accounting messages to the controller and the controller forwards these messages to an external AAA server.Note: Proxy Service must be enabled to display the MAC Registration and External MAC Auth options.
-
Click Add
Server and configure a new RADIUS Server. Refer to Adding and Managing a RADIUS Server.
-
Accounting
Service: Toggle the switch on to enable this option and select
the existing RADIUS Server from the drop-down list or complete the following
steps to add a new RADIUS Server.
- Click Add Server and configure a new RADIUS Server. Refer to Adding and Managing a RADIUS Server.
-
Proxy Service: Toggle the switch on to enable
the proxy service.
Note: Use the controller as a proxy in 802.1X networks. A proxy AAA server is used when APs send authentication/accounting messages to the controller and the controller forwards these messages to an external AAA server.
-
MAC
Authentication: Toggle the MAC
Authentication switch on.
Note: Enabling MAC Authentication displays MAC Registration list and External MAC Auth options.
Selection of MAC address format is not available for the MAC registration list.
With the 802.1X and MAC Authentication method, MAC authentication is the first layer of security—a list of authorized MAC addresses is configured on the network device first. Devices with MAC addresses that are not on the list are denied access to the network. The 802.1X authentication method uses a RADIUS server to verify the user’s identity (for example, username, password) before granting access to the network. A RUCKUS AP grants access to a UE only after both the MAC authentication and 802.1X authentication are successful.Note:- MAC Authentication provides an additional level of security for corporate networks. Client MAC addresses are passed to the configured RADIUS servers for authentication and accounting.
- By default, MAC Authentication is disabled.
- Changing the MAC Authentication option requires you to re-create the Enterprise AAA (802.1X) network. Currently, there is no edit option for this feature.
-
MAC Registration List: Select MAC
Registration List by clicking the radio button.
The MAC Registration List drop-down field is displayed.
-
MAC Registration
List: Select a MAC registration list from the drop-down list.
You can also add a new list by clicking Add.
The Add MAC Registration List dialog box is displayed. Complete the following to add a new MAC Registration List:Note: If MAC registration is enabled, RUCKUS One will process the initial authentication request using the MAC registration list. However, if the MAC registration list is not selected, the request will be handled by the AAA server instead.
- Name: Enter a name for the MAC Registration List.
- List Expiration: Select the expiration date for the list. Options include Never Expires, By Date (provide an expiration date for the list), or After (provide the hours or the number of days, weeks, months, or years after which the list will expire).
- Automatically clean expired entries: Toggle the switch on to clean expired entries in the list.
- Identity Group: Select an identity group from the drop-down list or add one by clicking Add. You can also enable Use single identity association to all onboarded devices to assign the same identity to all devices.
-
Adaptive
Policy Set: Select a policy set from the drop-down list
or add one by clicking Add.
Add MAC Registration List 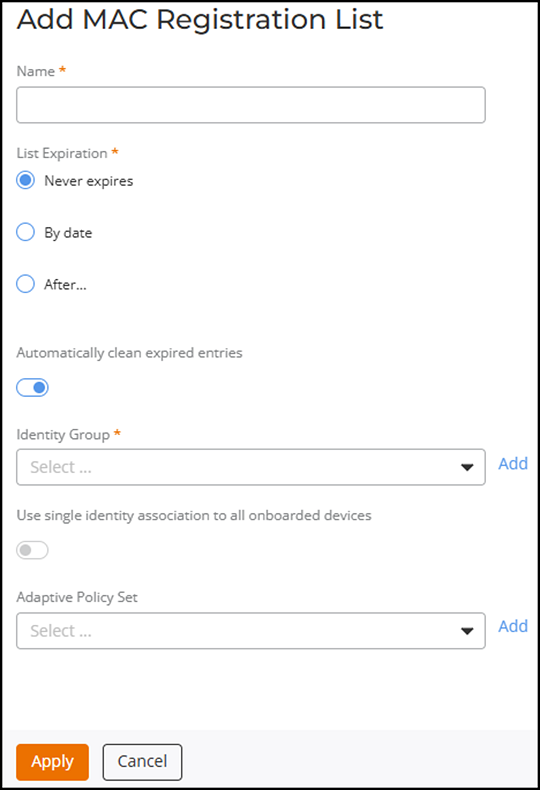
Note: Each SSID can be associated with only one MAC Registration List.Note: Adaptive policy sets configured with the MAC registration list will not be applied, as the external AAA authentication process occurs after the policy evaluation stage. -
External MAC Auth: Select External MAC
Auth by clicking the radio button.
The MAC Address Format drop-down field is displayed.
-
MAC Address Format: Select the MAC Address
Format from the drop-down list to enable external MAC
authentication. Supported MAC address formats are:
- Upper case MAC address separated by colons: 70:EA:5A:78:A1:A0
- Upper case MAC address separated by hyphens: 70-EA-5A-78-A1-A0
- Upper case MAC in a continuous string: 70EA5A78A1A0
- Lower case MAC address separated by colons: 70:ea:5a:78:a1:a0
- Lower case MAC address separated by hyphens: 70-ea-5a-78-a1-a0
- Lower case MAC in a continuous string: 70ea5a78a1a0
-
Click Show more
settings.
By default, the VLAN sub-tab is displayed. Each sub-tab includes additional Wi-Fi configuration options. Refer to Configuring Additional Settings for a Wi-Fi Network to configure each of the available settings.
Note:Demonstration of Advanced Settings for a Wi-Fi Network. This video explains advanced settings for a Wi-Fi network and walks you through the process of configuring them.
-
Click Next.
The Venues page is displayed.
Venues Page 
-
Select one or more venues where you want
to activate this network by clicking the checkbox next to the Venue column, and then toggle
the switch on in the Activated column.
The details in the APs, Radios, and Scheduling columns are displayed for all the activated venues. By default, this network configuration is applicable for All APs and their applicable radio bands, and is scheduled to be available 24/7.
-
Click the All APs hyperlink in the
APs column or the list of
radios in the Radios column of
the Venues section on the Create New Network
page to configure APs and radio-frequency bands for the selected venue.
The Select APs dialog box is displayed. Select one of the following options:
- All APs: Select
All APs to
activate this network on all current and future APs in this venue. Choose a radio
band from the drop-down list. You can choose one or more of the supported radio
bands.
Select APs 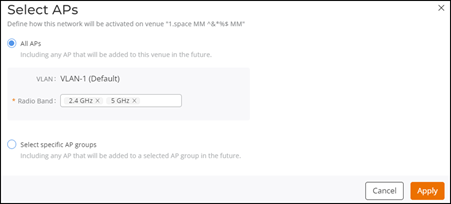
- Select specific AP
groups: Select Select specific AP
groups to activate this network on specific AP groups including any
AP that is added to the selected AP groups in the future. The APs not assigned to any
group option is displayed with a checkbox and a reminder to select
an AP Group.
Click the APs not assigned to any group checkbox; the VLAN and Radio Band options are displayed:
Select Specific AP Groups 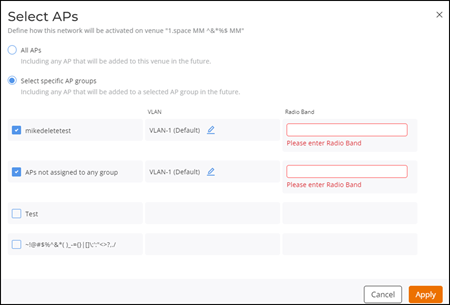
- In the VLAN option,
VLAN-1 is selected by default. Click the
 icon
and select VLAN or pool from the drop-down list. Depending on the selection, enter the
VLAN ID or select the pool from the drop-down list.
icon
and select VLAN or pool from the drop-down list. Depending on the selection, enter the
VLAN ID or select the pool from the drop-down list. - In the Radio Band option, select one or more of the supported radio bands from the drop-down list for the selected AP group.
- Click Apply.
- All APs: Select
All APs to
activate this network on all current and future APs in this venue. Choose a radio
band from the drop-down list. You can choose one or more of the supported radio
bands.
-
Click the 24/7 hyperlink in the
Scheduling
column of the Venues section on the Create New
Network page to customize the schedule.
The Schedule for Network <network-name> in Venue <venue-name> dialog box is displayed.
Schedule for Network Dialog Box 
- Click Custom Schedule.
- Customize the network schedule as
required. You can configure Monday through Sunday and times from 00:00 to 23:59.
Click the See tips hyperlink for guidance. The
Network Scheduler Tips dialog box is displayed.
Network Scheduler Tips 
- Review the tips and click OK to close the Network Scheduler Tips dialog box.
- Click Apply. The hyperlink updates to ON now. When hovered over, it displays the time until which the scheduler will remain active (<Day> <Time>).
-
Toggle the Network Tunneling switch on to
define how network traffic is tunneled at the venue. When toggled on, a Tunnel: <venue-name>
sidebar is displayed.
Note: The Network Tunneling switch is displayed only when the venue is Activated.
- Select a Tunneling Method from the drop-down.
- If you choose SoftGRE, select a
SoftGRE
profile and optionally enable and configure IPsec. (Refer to
Creating a SoftGRE Profile and Adding an SD-LAN Service).
The SD-LAN option is available only when RUCKUS Edge devices are present.
- Click Add to save and apply.
-
Click the All APs hyperlink in the
APs column or the list of
radios in the Radios column of
the Venues section on the Create New Network
page to configure APs and radio-frequency bands for the selected venue.
-
Click Next.
The Summary page is displayed.
-
Click Finish.
Network Summary 