Creating an Open Network
You can create a network that allows users to join the network without going through any authentication process.
-
On the navigation bar, select
Wi-Fi > Wi-Fi
Networks > Wi-Fi Networks
List.
The Wi-Fi Networks page is displayed.
-
Click Add Wi-Fi
Network. Alternatively, select an open network from the network list
by clicking the radio button next to the Name column, and
then click Clone.
The Create New Network page is displayed.
-
Complete the following fields
on the Network Details page.
- Network Name: Enter a name (2 to 32 characters) for a network. By default, this name is also used as the SSID.
- Set different
SSID: (Optional) Click Set different
SSID to configure an SSID different from the network
name. The SSID field is displayed.
- SSID: Enter an SSID name (2 to 32 characters).
- Description: Enter a description (up to 64 characters) to help you identify the network.
- Network
Type: Choose Open
Network.
A structure diagram of an Open Network is displayed.
Note: If you used the Clone option, the Network Type is already set to Open Network.
-
Click Next.
The Settings page is displayed.
Create New Network - Settings Page 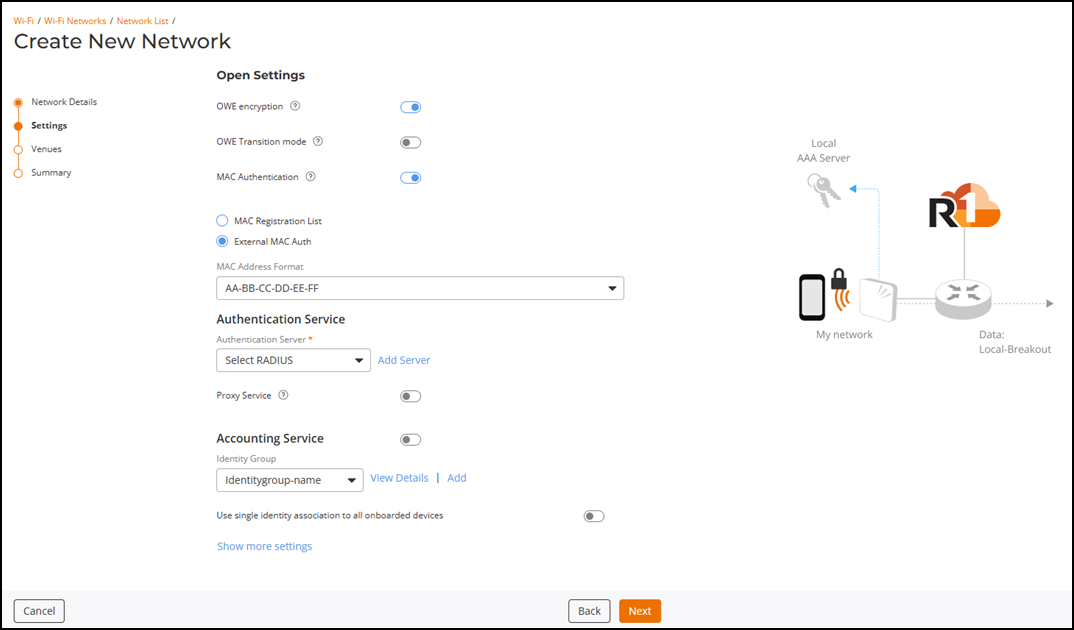
- Toggle the OWE encryption switch on to enable this feature and configure OWE Transition mode. The feature secures open Wi-Fi networks by encrypting data without needing passwords.
-
Toggle the OWE
Transition mode switch on to enable this feature.
The migration from an open Wi-Fi network to an enhanced open Wi-Fi network is completed gradually as user devices are upgraded. For STAs that do not support OWE authentication, the OWE transition mode is available so that such STAs can access the network in open authentication mode. Meanwhile, the OWE transition mode allows OWE-capable STAs to access the network in OWE authentication mode. The OWE transition mode is implemented as follows:
- Two SSIDs are created on an AP, for example, SSID 1 for open authentication and SSID 2 for OWE authentication.
- SSID 1 is broadcast, and
SSID 2 is hidden. Therefore, only SSID 1 is visible to STAs. SSID 1
carries an OWE Transition Mode element and SSID 2 information. When an
OWE-capable STA connects to SSID 1, it is directly associated with SSID
2 in OWE transition mode.
- Non-OWE-capable devices connect to SSID 1
- OWE-capable devices connect to SSID 2 through SSID 1
Note: The OWE transition WLAN allows you to broadcast the OWE SSID either on the 6 GHz radio band alone or across all the radio bands (2.4 GHz, 5 GHz, and 6 GHz) in a venue.Create New Network - Enabling OWE Encryption on the Settings Page 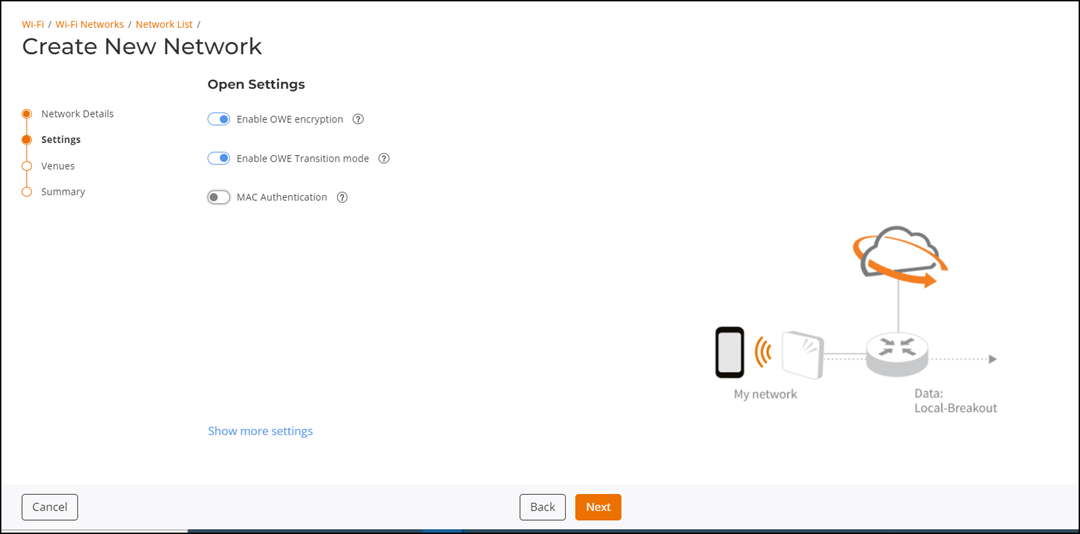
-
Toggle the MAC
Authentication switch on to enable this feature. This feature
provides an additional level of security for corporate networks. Client MAC
addresses are passed to the configured RADIUS servers for authentication and
accounting.
Configure MAC Authentication by selecting one of the options from the following:
- MAC Registration List
- External MAC Auth
Note:- After selecting either MAC Registration List or External MAC Auth, additional configuration fields will appear on the page to complete the MAC authentication setup.
- You cannot modify previously configured MAC authentication settings. To accommodate any modifications, you must create new MAC authentication settings.
- Regardless of whether MAC authentication is configured using MAC Registration List or External MAC Auth, the Dynamic VLAN setting is automatically enabled. The VLAN-related fields are displayed in the VLAN sub-tab when you click Show more settings.
- If you configured
MAC
Registration List, you will also have to configure a
new Identity profile (refer to Adding an
Identity) and associate it with a client device (refer to
Adding a Device
to an Identity).
Enabling MAC Authentication 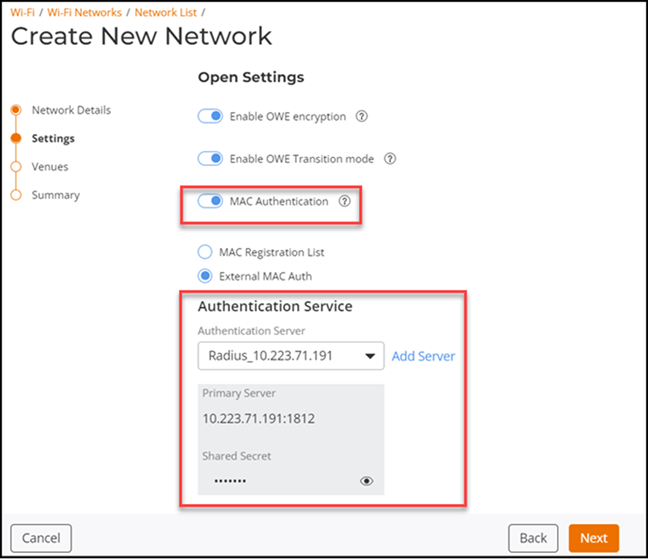
-
Select the MAC Registration
List from the drop-down list or click Add to create a
new MAC Registration.
The Add MAC Registration List dialog box is displayed.
Add MAC Registration List  Complete the following fields:
Complete the following fields:- Name: Enter a name for the MAC registration list.
- List
Expiration: Select one option from the following:
- Never expires: This list does not have an expiry date.
- By date: Select the date, month, and year. This list expires after the selected date.
- After: Select a number from the drop-down list and choose a duration (Hours, Days, Weeks, Months, or Years). The list expires after the selected duration.
- Automatically clean expired entries: Toggle switch on to enable this feature.
- Identity Group: Select an identity group from the drop-down list or click Add to create a new identity group. Refer to Adding an Identity Group.
- Use single
identity association to all onboarded devices:
Toggle switch on to enable this feature. An Identity Group
must be selected before this field becomes active. The Identity field is displayed.
- Identity: Select an identity from the drop-down list or click Add to create a new identity. Refer to Adding an Identity.
- Access Policy Set: Select an access policy set from the drop-down list or click Add to create a new access policy set. Refer to Creating an Adaptive Policy.
- Click Apply.
-
Select the External MAC Auth option
to configure external MAC authentication.
- Authentication Service: Select a RADIUS from the drop-down or click Add Server to add a new RADIUS authentication server. Refer to Adding and Managing a RADIUS Server.
- Proxy
Service: Toggle the switch on to enable the proxy
service.Note: Use the controller as proxy in 802.1X networks. A proxy AAA server is used when APs send authentication/accounting messages to the controller and the controller forwards these messages to an external AAA server.
-
Toggle the Accounting
Service switch on to enable this feature.
- Accounting Server: Select a RADIUS from the drop-down list or click Add Server to add a new RADIUS accounting server. Refer to Adding and Managing a RADIUS Server.
- Proxy
Service: Toggle the switch on to enable the proxy
service.Note: Use the controller as proxy in 802.1X networks. A proxy AAA server is used when APs send authentication/accounting messages to the controller and the controller forwards these messages to an external AAA server.
-
Identity Group:
Select an identity group from the drop-down list or click Add to create a
new identity group. Refer to Adding an Identity Group for
instructions on how to add an identity group.
Click View Details to view details about the identity group. The Identity Group sidebar is displayed with the following information: Description, Auto Clean-up, DPSK Service, MAC Registration, Certificate Template, and Adaptive Policy Set.Note:
- When an identity group is selected, all devices joining the network automatically become identities within that group, as shown on the Identity Group page.
- Users have the option to either select an existing identity group from the list or create a new one.
- Upon selecting an identity group, users can enable the Use single identity association to all onboarded devices option and subsequently choose a specific identity for association.
- If a single identity is associated, all devices joining the network are linked to the designated identity within the selected identity group.
- While editing the network, the initially selected identity group cannot be removed but can be changed to another identity group.
- The identity configuration section is not applicable to the MAC Registration List when MAC Authentication is enabled.
- If you select an Identity Group with the
Auto Clean-up feature disabled, a message
appears indicating that auto clean-up is disabled for the
selected identity group, which could result in excessive
identity creation per connected client device.
Create New Network - Configuring an Identity Group for Open Network 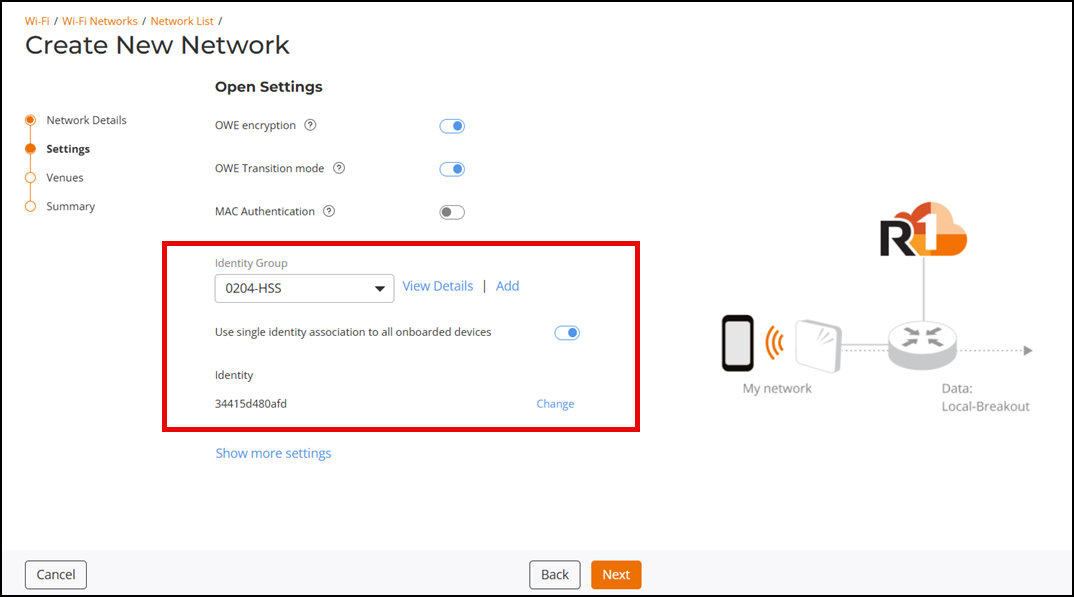
-
(Optional) Toggle the Use single identity
association to all onboarded devices switch on to enable this
option. The Identity section is displayed. If this option
is selected, all devices that connect to this network are associated with this
identity. If this option is not enabled, an identity for each connected device
is created under the identity group.
- Click Associate Identity to access the Associate Identity sidebar and select an identity to associate with the identity group, and then click Add.
- (Optional) Click Add Identity to access the Create Identity sidebar to add an identity. Refer to Adding an Identity for instructions on how to add an identity. Click Change to access the Associate Identity sidebar to select another identity.
-
Click Show more
settings.
By default, the VLAN sub-tab is displayed. Each sub-tab includes additional Wi-Fi configuration options for customizing network preferences. Refer to Configuring Additional Settings for a Wi-Fi Network to configure each of the available settings.
Note:Demonstration of Advanced Settings for a Wi-Fi Network. This video explains advanced settings for a Wi-Fi network and walks you through the process of configuring them.
-
Click Next.
The Venues page is displayed.
Venues 
-
Select one or more venues where you want
to activate this network by clicking the checkbox next to the Venue column, and then toggle
the switch on in the Activated column.
The details in the APs, Radios, and Scheduling columns are displayed for all the activated venues. By default, this network configuration is applicable for All APs and their applicable radio bands, and is scheduled to be available 24/7.
-
Click the All APs hyperlink in the
APs column or the list of
radios in the Radios column of
the Venues section on the Create New Network
page to configure APs and radio-frequency bands for the selected venue.
The Select APs dialog box is displayed. Select one of the following options:
- All APs: Select
All APs to
activate this network on all current and future APs in this venue. Choose a radio
band from the drop-down list. You can choose one or more of the supported radio
bands.
Select APs 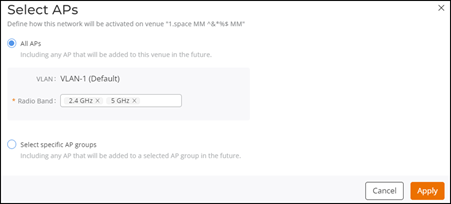
- Select specific AP
groups: Select Select specific AP
groups to activate this network on specific AP groups including any
AP that is added to the selected AP groups in the future. The APs not assigned to any
group option is displayed with a checkbox and a reminder to select
an AP Group.
Click the APs not assigned to any group checkbox; the VLAN and Radio Band options are displayed:
Select Specific AP Groups 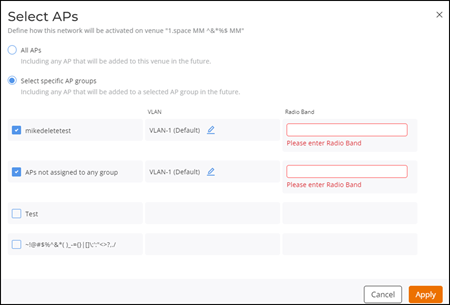
- In the VLAN option,
VLAN-1 is selected by default. Click the
 icon
and select VLAN or pool from the drop-down list. Depending on the selection, enter the
VLAN ID or select the pool from the drop-down list.
icon
and select VLAN or pool from the drop-down list. Depending on the selection, enter the
VLAN ID or select the pool from the drop-down list. - In the Radio Band option, select one or more of the supported radio bands from the drop-down list for the selected AP group.
- Click Apply.
- All APs: Select
All APs to
activate this network on all current and future APs in this venue. Choose a radio
band from the drop-down list. You can choose one or more of the supported radio
bands.
-
Click the 24/7 hyperlink in the
Scheduling
column of the Venues section on the Create New
Network page to customize the schedule.
The Schedule for Network <network-name> in Venue <venue-name> dialog box is displayed.
Schedule for Network Dialog Box 
- Click Custom Schedule.
- Customize the network schedule as
required. You can configure Monday through Sunday and times from 00:00 to 23:59.
Click the See tips hyperlink for guidance. The
Network Scheduler Tips dialog box is displayed.
Network Scheduler Tips 
- Review the tips and click OK to close the Network Scheduler Tips dialog box.
- Click Apply. The hyperlink updates to ON now. When hovered over, it displays the time until which the scheduler will remain active (<Day> <Time>).
-
Toggle the Network Tunneling switch on to
define how network traffic is tunneled at the venue. When toggled on, a Tunnel: <venue-name>
sidebar is displayed.
Note: The Network Tunneling switch is displayed only when the venue is Activated.
- Select a Tunneling Method from the drop-down.
- If you choose SoftGRE, select a
SoftGRE
profile and optionally enable and configure IPsec. (Refer to
Creating a SoftGRE Profile and Adding an SD-LAN Service).
The SD-LAN option is available only when RUCKUS Edge devices are present.
- Click Add to save and apply.
-
Click the All APs hyperlink in the
APs column or the list of
radios in the Radios column of
the Venues section on the Create New Network
page to configure APs and radio-frequency bands for the selected venue.
-
Click Next.
The Summary page is displayed.
- Review the settings that you configured.
- Click Finish.